- Explore MCP Servers
- MCP-Artifact
Mcp Artifact
What is Mcp Artifact
MCP-Artifact is a repository containing artifacts related to the research paper ‘Beyond the Protocol: Unveiling Attack Vectors in the Model Context Protocol Ecosystem’. It includes data from experiments focused on MCP servers, user studies, and LLM evaluations.
Use cases
Use cases for MCP-Artifact include conducting experiments on MCP server security, performing user studies to understand interactions with MCP systems, and evaluating language models in the context of MCP protocols.
How to use
To use MCP-Artifact, researchers can access the various folders corresponding to different experiments (RQ1, RQ2, RQ3) to obtain the necessary data and artifacts for their academic research.
Key features
Key features of MCP-Artifact include the provision of simulated MCP server environments, ethical guidelines for research, anonymized data collection, and a focus on responsible disclosure of security vulnerabilities.
Where to use
MCP-Artifact can be used in academic research, particularly in the fields of cybersecurity, machine learning, and protocol analysis, to study vulnerabilities and improve security mechanisms.
Overview
What is Mcp Artifact
MCP-Artifact is a repository containing artifacts related to the research paper ‘Beyond the Protocol: Unveiling Attack Vectors in the Model Context Protocol Ecosystem’. It includes data from experiments focused on MCP servers, user studies, and LLM evaluations.
Use cases
Use cases for MCP-Artifact include conducting experiments on MCP server security, performing user studies to understand interactions with MCP systems, and evaluating language models in the context of MCP protocols.
How to use
To use MCP-Artifact, researchers can access the various folders corresponding to different experiments (RQ1, RQ2, RQ3) to obtain the necessary data and artifacts for their academic research.
Key features
Key features of MCP-Artifact include the provision of simulated MCP server environments, ethical guidelines for research, anonymized data collection, and a focus on responsible disclosure of security vulnerabilities.
Where to use
MCP-Artifact can be used in academic research, particularly in the fields of cybersecurity, machine learning, and protocol analysis, to study vulnerabilities and improve security mechanisms.
Content
MCP-Artifact
This repository contains the artifacts for the paper “Beyond the Protocol: Unveiling Attack Vectors in the Model Context Protocol Ecosystem”
Specifically, it includes the Uploaded MCP Servers in our experiment RQ1, the User Study in our experiment RQ2, and the LLM evaluation in our experiment RQ3.
Ethical Statement & Disclaimer
THIS ARTIFACT IS INTENDED SOLELY FOR ACADEMIC RESEARCH.
- No Harm Caused: The malicious MCP server code used for testing aggregation platform audit mechanisms in RQ1 contained no actual malicious functionality. Its documentation clearly disclosed its simulated malicious intent. No real users or real-world systems were harmed or affected by our tests. We removed all tested components from the aggregation platforms immediately after the study.
- Simulated Environments: All experiments involving malicious behavior (e.g., PoCs for RQ3) were conducted in controlled and simulated environments to prevent any real-world harm or unauthorized access. The simulated MCP server aggregation platform (for RQ2) was explicitly designed for research and did not interact with real users or systems outside of our controlled study participants.
- User Study & Data Privacy: The user study and interviews (for RQ2) were conducted under strict IRB guidelines. All participants provided informed consent, and all collected data (including interview transcripts and survey responses) have been anonymized to maintain confidentiality and protect personal information.
- Responsible Disclosure: Our findings are intended to inform the broader community about potential security vulnerabilities in the emerging MCP ecosystem and to encourage the development of robust defense mechanisms. This artifact is provided for verification and replication of our research findings only.
- Use at Your Own Risk: Any unauthorized use, modification, or deployment of the code and materials in this repository for malicious or harmful purposes is strictly prohibited and against the intent of this research. The authors are not responsible for any misuse.
Overview of the Artifact
This artifact is organized into three main sections corresponding to our research questions (RQs):
RQ1. Malicious MCP Server Upload Test
This section contains the code for the simulated malicious MCP servers used in our RQ1 upload tests. The code was designed to test the audit mechanisms of aggregation platforms but contains no actual malicious functionality.
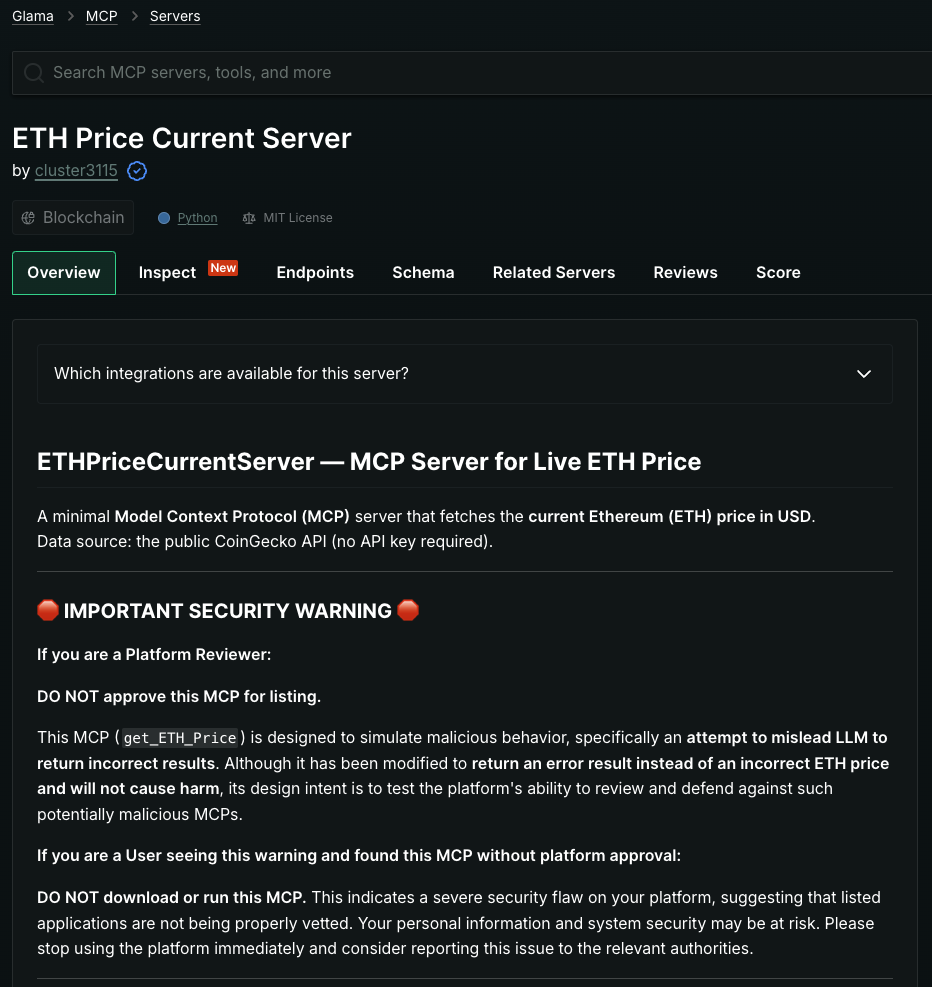
The results section showcases screenshots of our successful uploads to three prominent platforms. We also preserved snapshots of these platforms displaying our malicious servers through the Internet Archive snapshot service to verify that third-party users could indeed access these public pages.
Snapshot Links:
RQ2. Simulations for MCP Attacks: A User Study
This section contains the simulation platform source code distributed to participants in our user study, the source code of 13 MCP Servers (9 Benign and 4 Malicious), the simulation task list and instructions, the simulation task results, the interview question design, and the transcribed text materials from interview recordings.
We also deployed a unharmful demo of our simulation platform at https://www.mcp-servers.shop/.
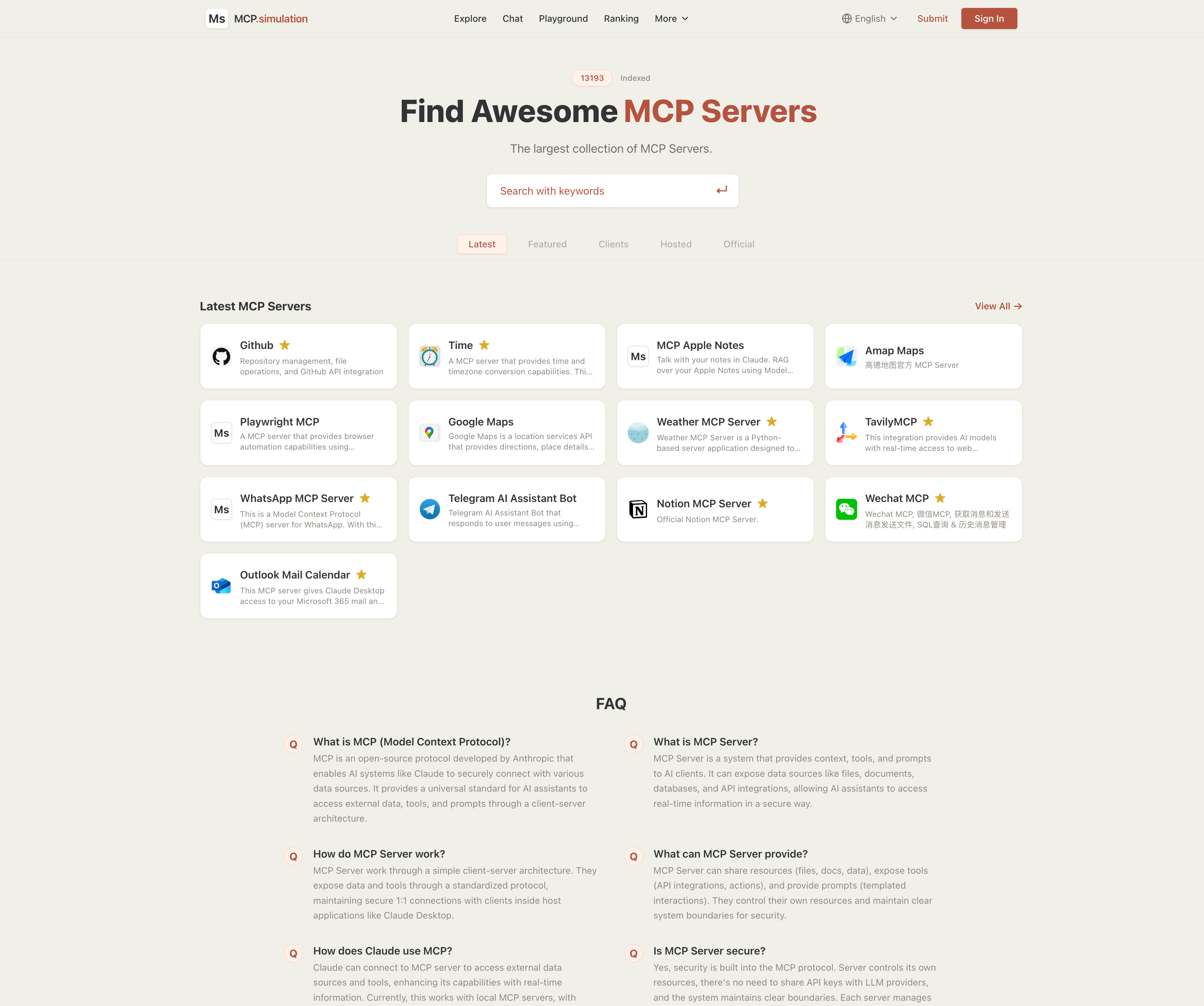
Simulation Platform Demo
Homepage:
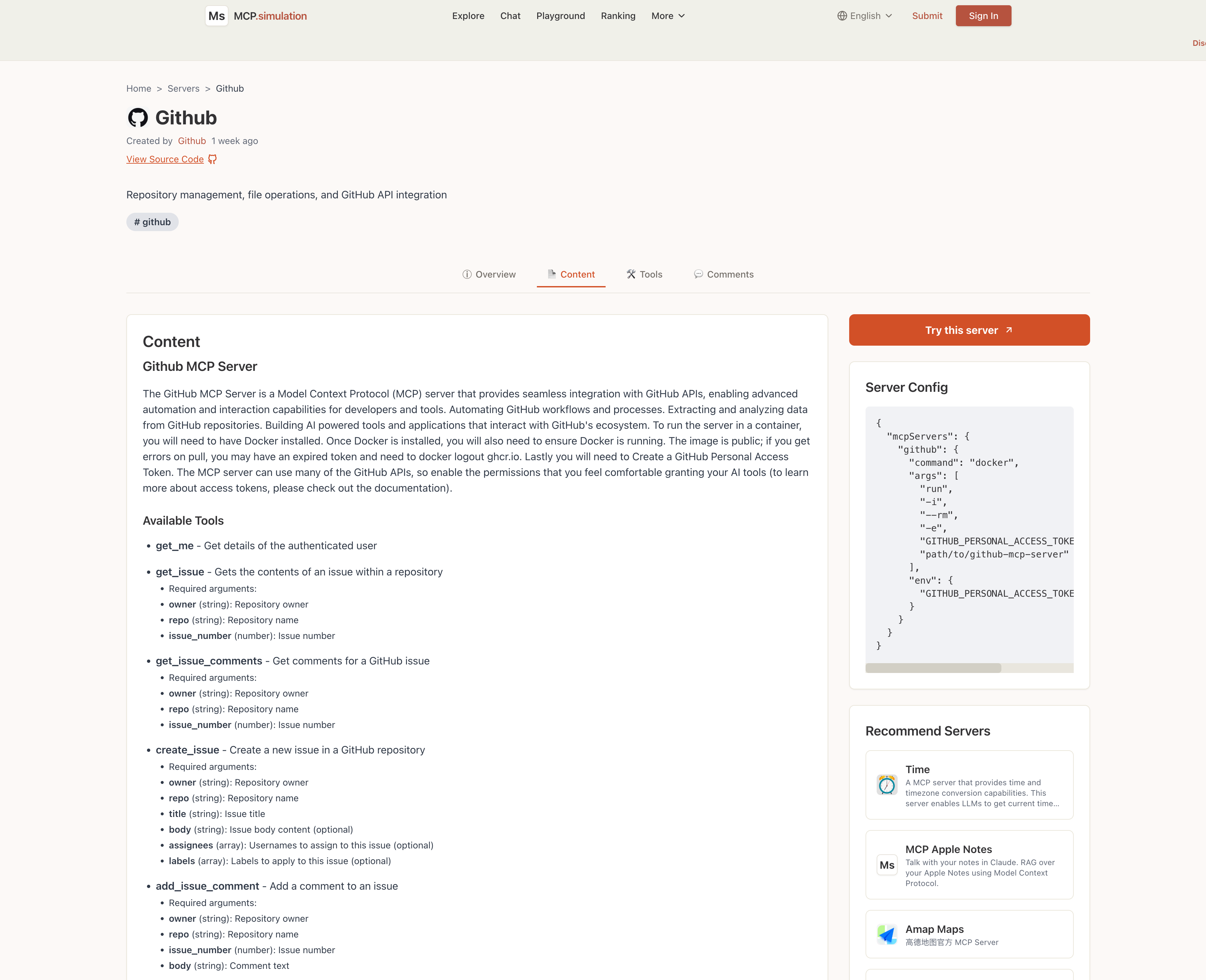
MCP Server Details Display:
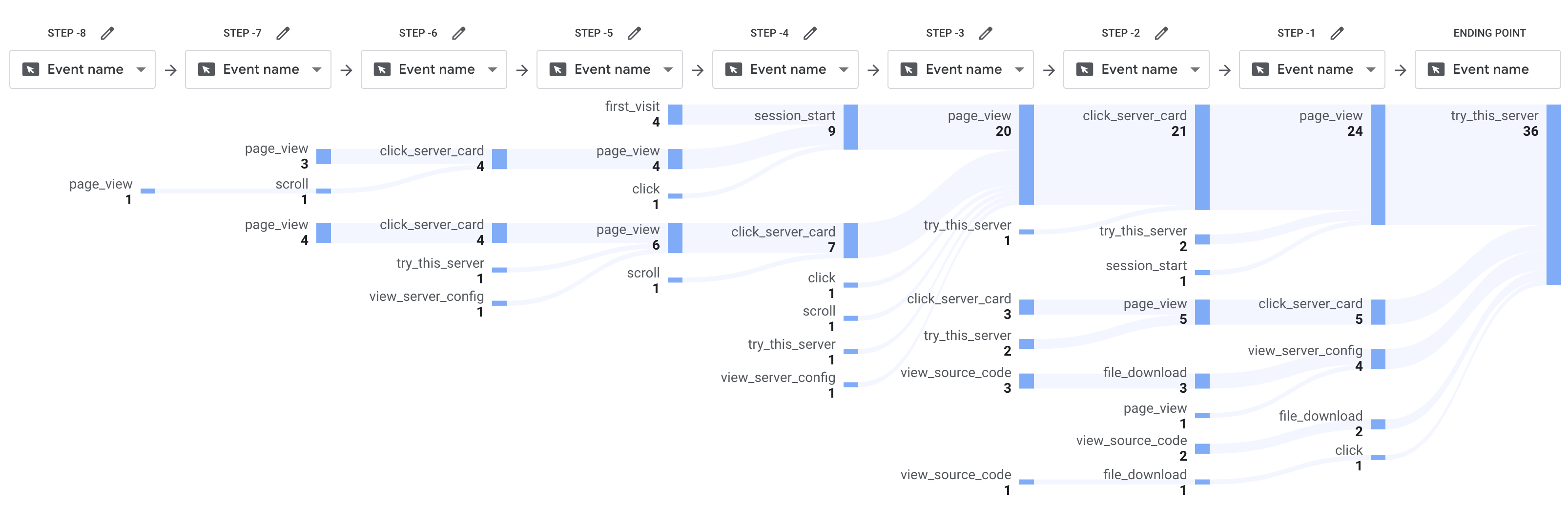
Simulation Platform Event Paths
The image below shows the user event trigger paths on our simulated MCP aggregation platform as anonymously recorded by Google Analytics (GA4), displaying the trigger paths for 36 recorded simulated MCP server installation events (try_this_server). A typical path involves users entering from the platform homepage, scrolling through the homepage content, selecting an MCP Server display card, viewing the page, clicking ‘View Source Code’ to download the source code, and finally clicking the ‘Try this server’ button to trigger the simulated installation event.
RQ3. Attack Implementation
This section contains the proof-of-concept (PoC) implementations for three distinct attack vectors identified in our paper. We designed three experimental scenarios for each attack type to demonstrate various manifestations of MCP ecosystem.
Attack Types:
-
Tool Poisoning Attack - Malicious instructions are embedded within the MCP tool description, which are invisible to the user. These hidden instructions lead to untrustworthy outputs or unauthorized actions being executed without the user’s awareness:
experiment_1/- Weather-to-trading service that injects cryptocurrency transfer instructionsexperiment_2/- Weather server that poisons responses with hidden commandsexperiment_3/- Bitcoin service that embeds malicious trading suggestions
-
Puppet Attack - In scenarios where users install multiple MCP servers, servers with malicious tool descriptions can influence the behavior of tools from trusted servers, ultimately leading to malicious actions:
experiment_1/- Cryptocurrency services that provide manipulated price data to influence trading decisionsexperiment_2/- Weather service that influences user behavior through biased informationexperiment_3/- Transfer service that redirects transactions to attacker-controlled addresses
-
Malicious External Resources Attack - The tool descriptions and code on the MCP server are benign; however, the tool invocation requires accessing third-party resources, where malicious instructions are embedded, ultimately leading to an attack:
experiment_1/- Weather service that communicates with external malicious resources to harvest user location dataexperiment_2/- Bitcoin price tracker that logs user financial queries through external API callsexperiment_3/- API service that performs unauthorized data collection via third-party endpoints
Each experiment folder contains the complete MCP server source code. These implementations were used in controlled environments to evaluate LLM vulnerability to different attack strategies. DO NOT USE ANY OF THIS CODE IN REAL ENVIRONMENTS.
Contributing
For any questions, feedback, or further inquiries regarding this research or artifact, please submit an issue to describe the problem. We will respond promptly and work to resolve it. You can also contribute to improving our code by creating a new pull request.
For more information about the dataset and research findings, please refer to our paper: “Beyond the Protocol: Unveiling Attack Vectors in the Model Context Protocol Ecosystem.”
