- Explore MCP Servers
- fastmcp-python-oauth2-with-entra-id
Fastmcp Python Oauth2 With Entra Id
What is Fastmcp Python Oauth2 With Entra Id
fastmcp-python-oauth2-with-entra-id is an example implementation of the MCP authorization specification that utilizes Microsoft Entra ID as a third-party authorization server. It demonstrates how to secure an MCP server using OAuth2 authentication.
Use cases
Use cases include securing access to user-specific data in MCP tools, demonstrating OAuth2 flows in educational contexts, and providing a foundation for building secure applications that require third-party authorization.
How to use
To use fastmcp-python-oauth2-with-entra-id, set up an Entra App registration, enable public client flows, and configure the redirect URI. The server can then be accessed through the provided console-based client, which authenticates using the OAuth2 Authorization Code flow.
Key features
Key features include OAuth2 Bearer token protection, a demonstration tool for accessing user information, and a complete OAuth2 flow from authentication to resource access.
Where to use
fastmcp-python-oauth2-with-entra-id can be used in applications requiring secure user authentication and authorization, particularly in environments that utilize Microsoft Entra ID for identity management.
Clients Supporting MCP
The following are the main client software that supports the Model Context Protocol. Click the link to visit the official website for more information.
Overview
What is Fastmcp Python Oauth2 With Entra Id
fastmcp-python-oauth2-with-entra-id is an example implementation of the MCP authorization specification that utilizes Microsoft Entra ID as a third-party authorization server. It demonstrates how to secure an MCP server using OAuth2 authentication.
Use cases
Use cases include securing access to user-specific data in MCP tools, demonstrating OAuth2 flows in educational contexts, and providing a foundation for building secure applications that require third-party authorization.
How to use
To use fastmcp-python-oauth2-with-entra-id, set up an Entra App registration, enable public client flows, and configure the redirect URI. The server can then be accessed through the provided console-based client, which authenticates using the OAuth2 Authorization Code flow.
Key features
Key features include OAuth2 Bearer token protection, a demonstration tool for accessing user information, and a complete OAuth2 flow from authentication to resource access.
Where to use
fastmcp-python-oauth2-with-entra-id can be used in applications requiring secure user authentication and authorization, particularly in environments that utilize Microsoft Entra ID for identity management.
Clients Supporting MCP
The following are the main client software that supports the Model Context Protocol. Click the link to visit the official website for more information.
Content
MCP Server Authorization Example (OAuth2 + Entra ID)
This demonstration shows how to secure an MCP server using the MCP Authorization specification with Entra ID as a third party authorization server. This example includes an implementation of OAuthAuthorizationServerProvider from the MCP Python SDK tailored for Microsoft Entra ID.
Server Functionality
The MCP server provides a demonstration tool called get_user_name that showcases how authenticated user information can be accessed within MCP tools. This tool:
- Requires Authentication: The tool can only be invoked after successful OAuth2 authentication with Entra ID
- Returns User Information: Provides the user’s display name as obtained from their Entra ID profile
- Demonstrates Authorization Flow: Shows how the MCP Authorization specification enables secure access to user-specific data
This simple tool demonstrates the complete OAuth2 flow from authentication through to accessing protected resources with user context.
This solution is for demonstration purposes only and is not suitable for production use cases. In some cases, code comments highlight areas that require attention.
Components
- Server:
azure_user_mcp_server.py- Implements an MCP server protected by OAuth2 Bearer tokens (Entra ID).
- Client:
simple_oauth_client_example.py- Console-based client that authenticates with the MCP server using the OAuth2 Authorization Code flow (with PKCE).
Environment Setup
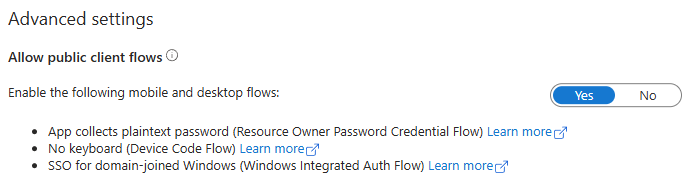
Create an Entra App registration and enable public client flows in the Authentication options. This ensures the server doesn’t require secrets when doing the token exchange.
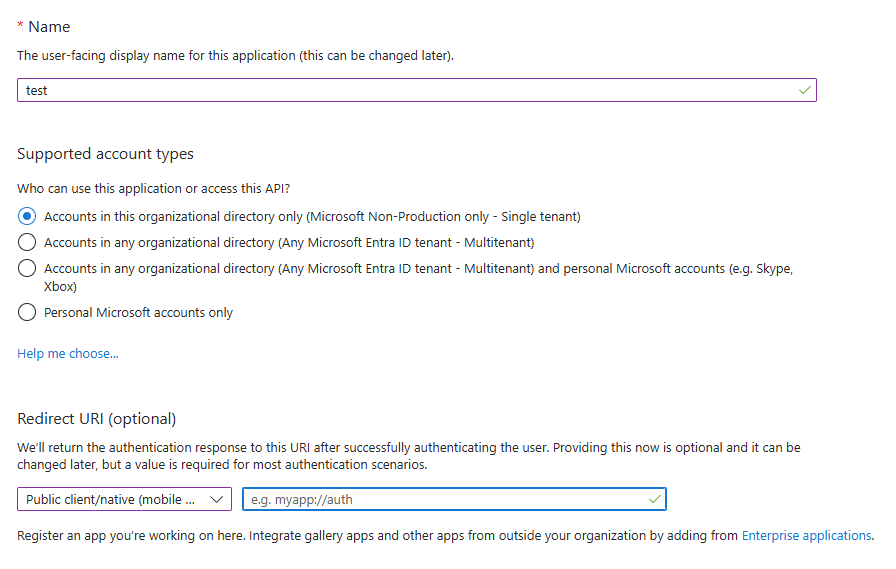
- Set
http://localhost:8000/auth/callbackas a the redirect URI.
Create a .env file in the project root with the following variables:
AUTH_TENANT_ID=your-tenant-id AUTH_CLIENT_ID=your-client-id # Optional: # AUTH_AUTHORITY=login.microsoftonline.com # AUTH_REDIRECT_URI=http://localhost:8000/auth/callback
AUTH_TENANT_ID: Your Entra ID (Azure AD) tenant IDAUTH_CLIENT_ID: The client/application ID registered in Entra IDAUTH_REDIRECT_URI: Redirect URI for the MCP server (default:http://localhost:8000/auth/callback)
How to Run the Demo
-
Install dependencies:
pip install uv uv sync -
Start the MCP Server:
From the project root, run:make start-server -
Run the OAuth2 Console Client:
In a new terminal, from the project root, run:make start-clientThe client will:
- Attempt to access the protected resource (expecting 401)
- Initiate the OAuth2 Authorization Code flow
- Print the authorization URL to the console (open in browser to authenticate)
- Handle the callback and exchange the code for a token
- Connect to the server and allow the user to interact with the MCP server via common functions such as listing available tools and invoking a tool.
Using MCP Inspector to Access the MCP Server
MCP Inspector is a graphical tool for interacting with MCP servers.
-
Installation:
- Follow the official installation instructions on the MCP website: MCP Inspector Installation Guide
-
Authentication:
- Launch MCP Inspector after installation.
- Connect to the MCP server at the appropriate URL (e.g.,
http://localhost:8000/sse).
This allows you to interact with the secured MCP server using the graphical interface, authenticated with a valid OAuth2 token.
Notes
-
Azure Application Registration Required: Before running this demo, you must create an application registration in Microsoft Entra ID (Azure AD). This registration provides the
AUTH_CLIENT_IDandAUTH_TENANT_IDvalues needed in your.envfile. -
Setup Instructions: For detailed steps on creating an application registration and configuring redirect URIs follow the official Microsoft documentation: Register an application with Microsoft identity platform
-
Redirect URI Configuration: Ensure your application registration includes
http://localhost:8000/auth/callbackas a valid redirect URI in the authentication settings.
DevTools Supporting MCP
The following are the main code editors that support the Model Context Protocol. Click the link to visit the official website for more information.










